Originally Posted on Blacklist Monitoring with RBLTracker.
Since our inception, we’ve helped thousands of companies and individuals, from all around the world, stay on top of day-to-day threats related to their email and websites. Recently, with the addition of our Facebook Threat Exchange monitoring, we’re helping those same customers battle social media related threats.
Some of our earliest customers have been cloud hosting and cloud computing companies- companies that provide the backbone of the Internet as we know it today.
Cloud Hosting Providers
One specific challenge with this type of company, is the sheer number of IP addresses and domains to monitor, and the regular re-use of these IP addresses. The last thing you want, is a brand new customer getting an IP address that is already blacklisted because of something the last owner did.
Another key challenge, is making sure that resources are used “only as needed”. Let’s face it- you don’t want to pay to monitor hosts that aren’t being used- and you shouldn’t have to.
We offer a few key features that makes blacklist monitoring for cloud hosting providers, easier and more affordable.
IP Range Host Type
Normally customers add IP addresses and domains (aka “Hosts”) to the RBLTracker portal individually. If you have 10 to 15 Hosts, this isn’t really a big deal. You can add hosts using our bulk loader, or individually. You can also add Hosts as a range or CIDR block (x.x.x.x/y).
But what if you have thousands of Hosts to monitor? At some point it’s going to become unwieldy to provision, and impossible to manage.
To support this, we built a custom “IP Range” Host type. This lets you add IP addresses as a range or CIDR block, but rather than thousands of IP addresses showing under your account, a single Host entry is shown. Our system will still monitor every single IP address individually– but the full block of IP addresses can be managed as a single entry.
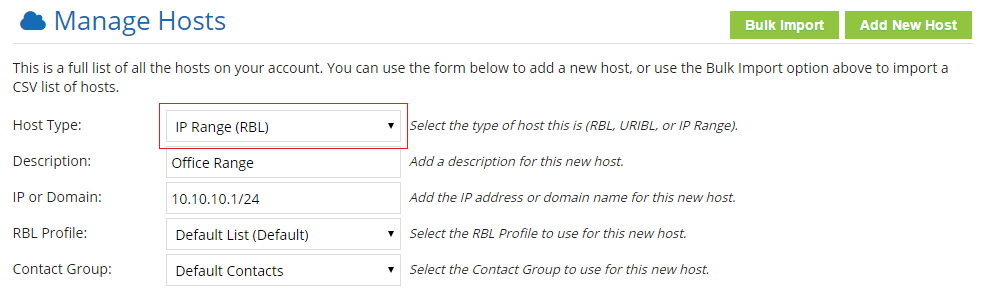
So whether you have a few /24’s or a whole /18- you can easily manage the full IP block with ease.
API Provisioning
Loading all your IP addresses into the system is great, but what if you only want to monitor a sub-set of those hosts? Or if you only want to enable monitoring for hosts that are currently in-use?
Several of our customers have opted to integrate with our web-based API, to provision monitoring on IP addresses as they’re allocated to their customers. That way only active IP addresses are being monitored. This ensures that you’re only paying for monitoring that matters- that will actually impact your business or your customers.
The RBLTracker API is easily integrated into any provisioning or monitoring platform, with just a few simple lines of code:
# wget --post-data="type=rbl&name=Test&host=10.10.10.10" -qO- https://rbltrack.com/api/host/add.json?api_token=x
{
"status_code": 200,
"status_message": "Hosts added successfully.",
"data": [
{
"id": "37c46a725dd8adab28d35b9f200c198d",
"host": "10.10.10.10",
"name": "Test"
}
],
"version": "2.0"
}
Easily enable monitoring on a Host when it’s allocated to a customer, and then disable it when it’s de-allocated- it’s a simple as that.
Contact Groups
When we identify an issue with any of your Hosts, we’ll immediately notify you via several different notification methods. These contacts can be broken down into custom contact groups, and assigned to Host. The end result, is that you can have a unique contact for every host under your account:
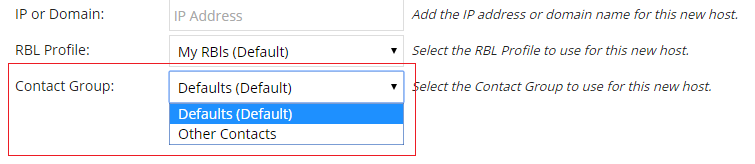
Cloud Hosting companies can optionally send alerts directly to their customers, notifying them about issues with their IP addresses and domains, and alleviating some of the burden from their network operations staff.
We regularly add new features and tools to make managing and provisioning monitoring services, easier and more effective for our customers.
![]()

 DMARC, or “Domain-Based Message Authentication, Reporting, and Conformance”, allows a domain owner to publish policies in DNS, telling remote mailers what to do with messages that do not align with these polices. DMARC is built on top of two existing technologies:
DMARC, or “Domain-Based Message Authentication, Reporting, and Conformance”, allows a domain owner to publish policies in DNS, telling remote mailers what to do with messages that do not align with these polices. DMARC is built on top of two existing technologies: