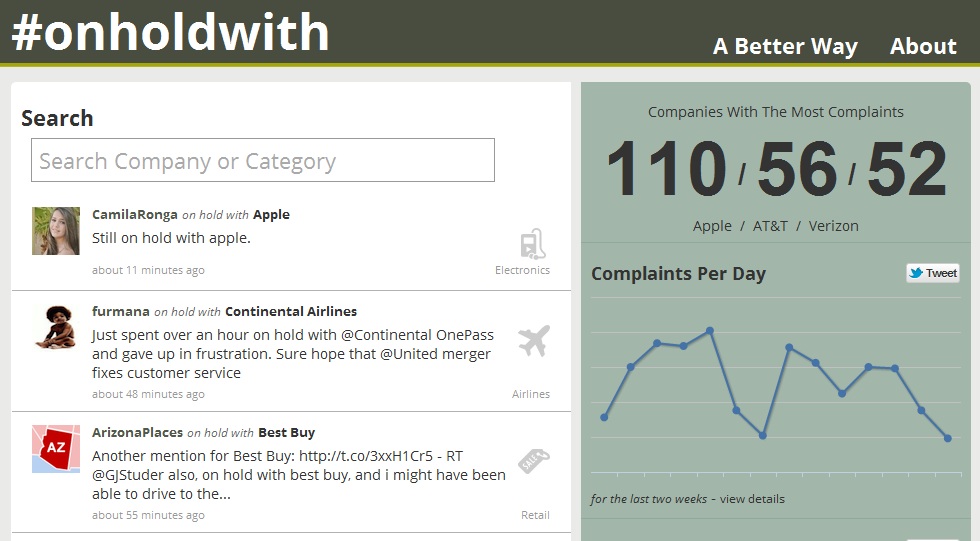
Is your email secure?
The default behavior of POP3 and IMAP, is to pass your username and password (and all your e-mail for that matter) over a socket with no encryption. This means that all that information is susceptible to a “man in the middle” type attack, where the plain text packets can be intercepted and read.
Is that really going to happen? Probably not, but you can avoid it, by setting up your e-mail servers to provide SSL encryption for all incoming and outgoing email.
This post will talk only about the mail server software I use: Exim (SMTP), Dovecot (POP3 & IMAP) and Perdition (for POP3/IMAP proxying / load balancing).
SSL vs. TLS vs. STARTTLS
First off, there’s a lot of confusion around the naming conventions.
TLS (Transport Layer Security) is SSL- technically, TLS version 1 is SSL version 3. The use of SSL v1 and v2 should be avoided if not completed disabled, so for all intents and purposes, when we say “SSL”, we mean SSL v3.
SSL uses separate dedicated ports for mail: 993 for secure IMAP, 995 for secure POP3 and 465 for secure SMTP. The encrypted connection is negotiated immediately after the socket is opened, and all communication is encrypted. This is more attune to how HTTPS works. The downside with this implementation, is that the service is provided on different ports, which may mean changes to your firewall rules, ACL’s and mail clients.
STARTTLS is a command implementation that works on the existing IMAP, POP3 and SMTP ports. The email client connects to the normal unencrypted ports, and uses a plain text command (STARTTLS in SMTP and IMAP, and STLS in POP3) to initiate a TLS (SSLv3) connection. From that point on, all communication is encrypted. The plus with this, is that the service works over the existing ports, so no firewall or ACL changes are needed.
A big part of the confusion comes from the mail clients, as they all seem to refer to the implementations with different names:
http://en.wikipedia.org/wiki/Comparison_of_e-mail_clients#SSL_and_TLS_support
In a lot of cases, the options are between “SSL” and “TLS”; SSL being an SSLv3 (TLS) connection on the different ports, and TLS meaning a STARTTLS connection. So for this post, we’ll use the same language.
We’re going to setup both (SSL and STARTTLS), which gives us the most flexibility with our clients, though technically, having dedicated ports for SSL services was deprecated in favor of STARTTLS, as it was thought that using two different ports for plaintext and SSL connections seemed wasteful.
Certificates
For our purposes, we’re just going to use a self-signed certificate for e-mail. This provides the same encryption as a certificate bought from a trusted authority- the only difference is the trust part. Obviously, if you’re going to set this up for customers or for the general public, a trusted authority is better, as you won’t receive any of those annoying trust errors when connecting.
There’s a million tutorials out there that show you how to create a self-signed certificate, so I won’t go on too much about this. There’s even a handy site that will generate it for you online.
http://www.selfsignedcertificate.com/
Create the key:
openssl genrsa -out mail.example.com.key 2048
Create the certificate:
openssl req -new -x509 -key mail.example.com.key -out mail.example.com.crt -days 3650 -subj /CN=mail.example.com
Exim
The SSL config for Exim is pretty straight forward:
tls_advertise_hosts = *
tls_on_connect_ports = 465
tls_certificate = /path/to/ssl/mail.example.com.crt
tls_privatekey = /path/to/ssl/mail.example.com.key
This basically says to advertise STARTTLS to everybody (*), to assume connections on port 456 are SSL connections, and use the certificate and key files referenced.
To make SSL work on port 465, you’ll need to tell Exim to also listen on that port. This would likely require adding another entry to your “local_interfaces” option- something like:
local_interfaces = 192.168.0.1.25:192.168.0.1.587:192.168.0.1.465
Restart Exim, and SSL should work. More information can be found here.
Dovecot
Dovecot provides POP3 and IMAP services, and supports both SSL and STARTTLS. The setup, again, is pretty straight forward:
protocols = imap pop3 imaps pop3s
ssl = yes
ssl_cert = </path/to/ssl/mail.example.com.crt
ssl_key = </path/to/ssl/mail.example.com.key
Restart Dovecot and test. More information can be found here.
Perdition
Perdition is a mail retrieval proxy. It handles load balancing and load distribution of POP3/IMAP connections, by proxying based on database or regex lookups. One other nice feature of Perdition, is that it can offload the encryption handling of mail connections. It can handle the SSL/STARTTLS negotiation, and then proxy the connections to local servers unencrytped, which reduces the overhead on the actual mail servers.
In my system, I use Perdition to load balance mail between multiple mail servers, as well as handle all the encryption/decryption.
Copy your imap4 and pop3 config files to new imap4s and pop3s config files, and change each, respectively, to:
protocol IMAP4S
and
protocol POP3S
and then add to each:
ssl_mode ssl_listen
ssl_cert_file /path/to/ssl/mail.example.com.crt
ssl_key_file /path/to/ssl/mail.example.com.key
Now, like I said before, in my case I only listen for encrypted connections with Perdition, then I relay mail internally over a non-encrypted link. Perdition has all sorts of ssl_mod options for handling different setups.
In my existing imap4 and pop3 config files I also added:
ssl_mode tls_listen
ssl_cert_file /path/to/ssl/mail.example.com.crt
ssl_key_file /path/to/ssl/mail.example.com.key
Telling it to listen for STARTTLS requests on the non-secure IMAP and POP3 ports.
Restart your existing IMAP4 and POP3 servers, and then start two new perdition instances, using the new IMAPs and POP3s config files.
Testing
The easiest way to test is to use the OpenSSL command line “s_client”, which lets you connect to encrypted services as a client, and validate that the SSL config is working.
IMAPs (SSL)
openssl s_client -connect mail.example.com:993
IMAP + STARTTLS
openssl s_client -connect mail.example.com:143 -crlf -starttls imap
POP3s (SSL)
openssl s_client -connect mail.example.com:995
POP3 + STARTTLS
openssl s_client -connect mail.example.com:110 -crlf -starttls pop3
SMTPs (SSL)
openssl s_client -connect mail.example.com:465
SMTP + STARTTLS
openssl s_client -connect mail.example.com:25 -crlf -starttls smtp
Adding encryption to your mail system is easy, and pretty much every mail client supports either SSL or STARTTLS, if not both.